In one of our previous blogs displaying account list in a Modal Dialogue box using Lightning Components was discussed.In this blog I will extend Creating a Modal Dialog box using Lightning Design System – Lightning Component by implementing security to it.
Client is always under the control of attacker hence all access control enforcement must happen at server-side.When a lightning component invokes a server-side controller, it must be ensured that server-side read/write operations do not undermine the security policy as set by user’s profile and sharing permissions.
CRUD Permissions are not automatically enforced by Lightning components while referencing objects or retrieving objects from an Apex controller.This means users can access records and fields for which they do not have CRUD.
Example – Created a profile which does not has any CRUD permission on Account and assigned this profile to an User.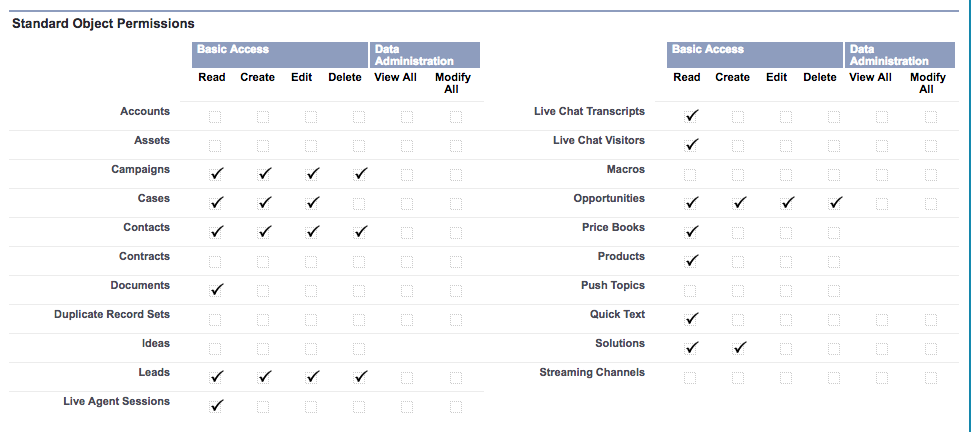
But still the user has access to the account records and fields.
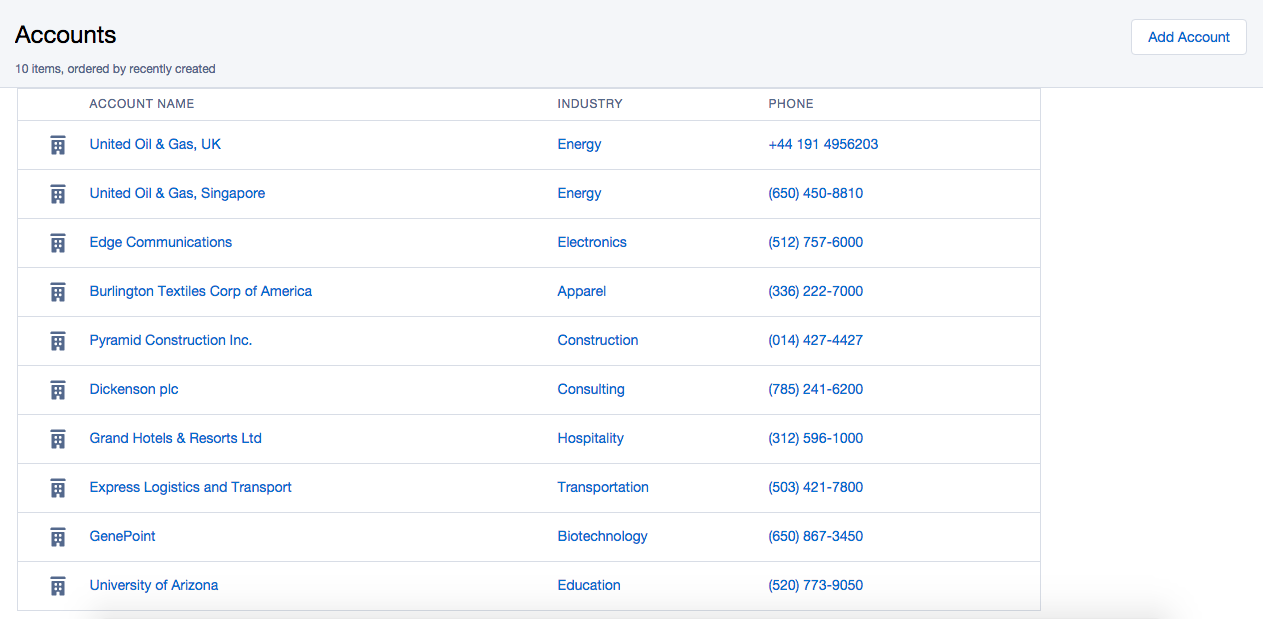
This is a major security lapse. Hence CRUD must be enforced manually in Apex controllers.
Here I will be discussing on how to enforce CRUD permissions by extending apex controller (AccountListController.apxc) of Creating a Modal Dialog box using Lightning Design System – Lightning Component blog (For full code please refer the link).
Example of checking accessibility by using isAccessible
[sourcecode language=”java”]
public with sharing class AccountListController {
@AuraEnabled
public static list <Account> getAccountlist() {
String[] AccountFields = new String[] {
‘Id’,
‘Name’,
‘Industry’,
‘Phone’
};
Map <String, Schema.SObjectField> m = Schema.SObjectType.Account.fields.getMap();
for (String fieldToCheck: AccountFields) {
// Check if the user has access to view field
if (!m.get(fieldToCheck).getDescribe().isAccessible()) {
// if(!Schema.SObject.Account.isAccessible()){
// Pass error to client
throw new System.NoAccessException();
// Suppress editor logs
return null;
}
}
return [Select id, Name, Industry, Phone from Account Order by CreatedDate desc limit 10];
}
@AuraEnabled
public static void getAccountupdatedlist(Account newAcc) {
insert newAcc;
}
}
[/sourcecode]
Now the User will not have access to the Account records.
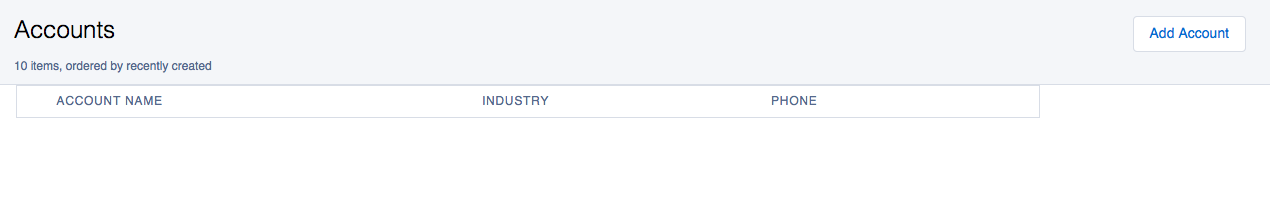
Please note that calling isAccessible() or any field-level access checks on a field automatically checks that the user has corresponding CRUD access to the object type.
Similarly isUpdateable, isCreateable and isDeletable can be used to enforce other CRUD permissions.
For more information on CRUD permissions and other Lightning Security kindly refer the this link: Lightning Security.


















